The Safe Shepherd Blog
How to Opt Out of CheckPeople - Step by Step Guide
In an era where our personal information is readily accessible online, maintaining privacy can be challenging. CheckPeople is one of the many data brokers that compile personal information, making it searchable online. If you're concerned about your privacy and looking to opt out of CheckPeople, this step-by-step guide is for you.
Step 1: Go to the CheckPeople Opt-Out Page
Start by visiting CheckPeople's opt-out page here: https://checkpeople.com/do-not-sell-info.
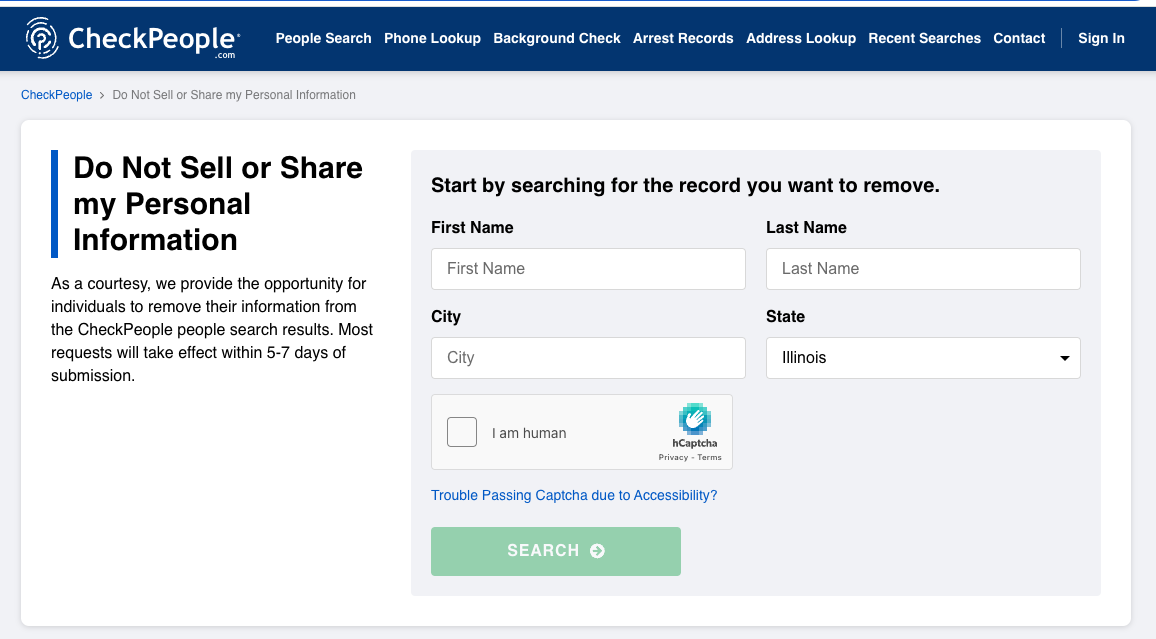
Step 2: Fill Out the Opt-Out Form
Fill in the data requested and press the Search button. If CheckPeople has your information, you should see a screen like this.
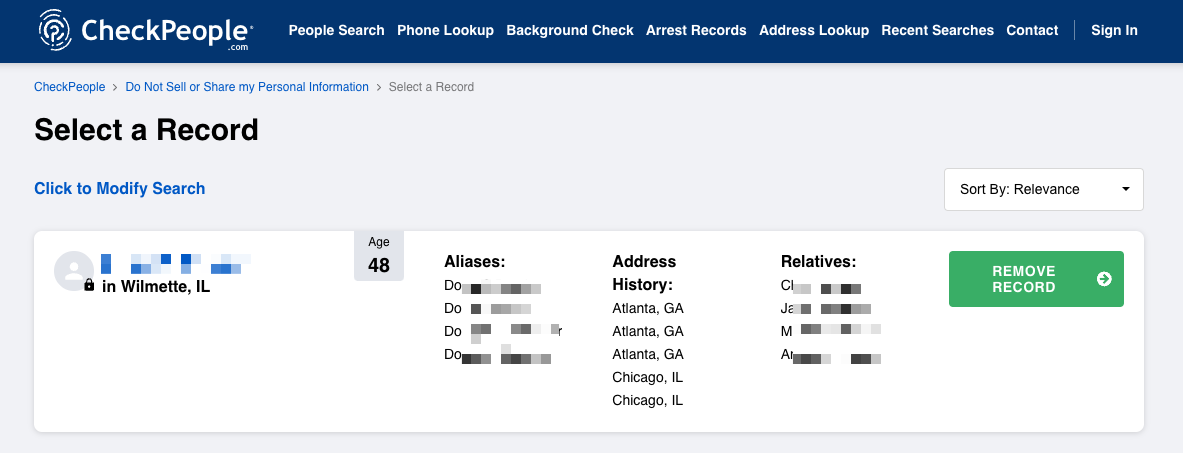
Click “Remove Record” to submit your opt-out request.
Step 3: Verification
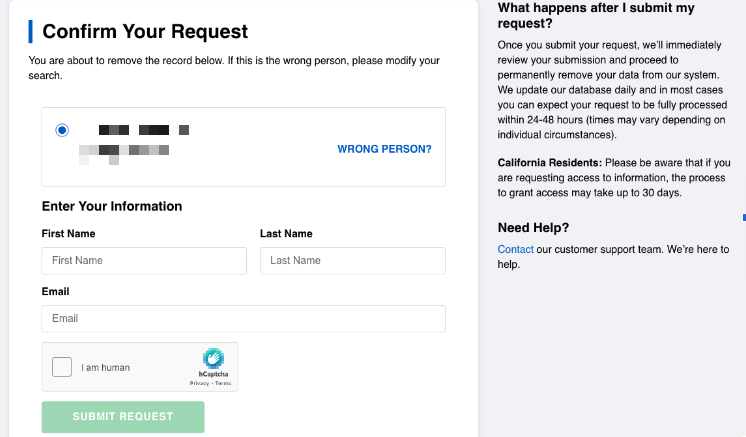
After submitting your request, CheckPeople will ask for your email so they can verify your identity. This step ensures that the request is legitimate and protects your information from fraudulent opt-out requests.
Fill in the verification form and press the Submit Request button.
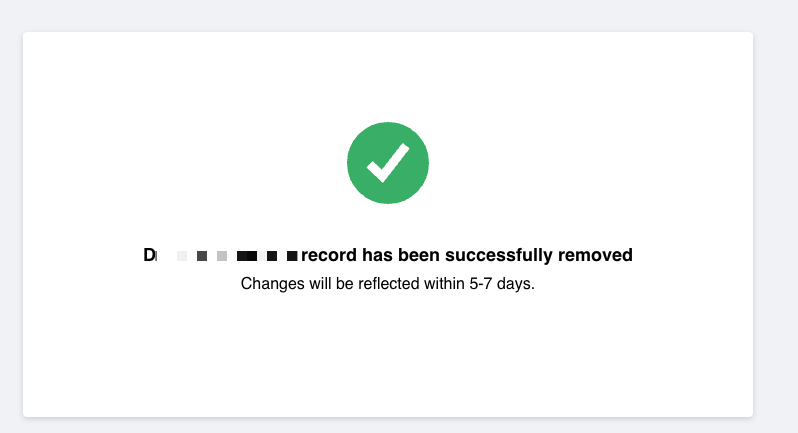
Step 4: Confirmation and Follow-Up
Once your request is verified, you will see the confirmation screen below. It may be beneficial to follow up after the communicated time to see if your information has been removed.
Step 5: Regular Checks
Data brokers often update their databases with new information. Regularly check to see if your information reappears on CheckPeople and repeat the opt-out process if necessary.
Why SafeShepherd.com Is Your Ally in Privacy
While opting out individually from sites like CheckPeople is a step towards safeguarding your privacy, it's a cumbersome process that needs to be repeated across numerous data brokers. SafeShepherd.com offers a streamlined solution to this problem. By signing up for SafeShepherd's service, you get a dedicated privacy advocate who will manage opt-outs on your behalf, not only from CheckPeople but from a wide array of data brokers. This proactive approach ensures that your personal information stays out of public databases, giving you peace of mind and freeing up your time to focus on what matters most to you.